
Extension Auditor - Security & Privacy Analyzer
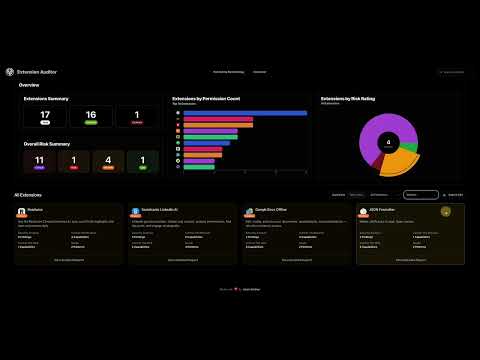


Overview
Analyze and monitor browser extensions for security and privacy risks. Get instant risk assessments and stay safe online.
Overview In today’s threat landscape, even trusted browser extensions can be compromised. Recent high-profile incidents like the Cyber Haven breach on Christmas Eve 2024 have shown that attackers can bypass even robust security measures. Extension Auditor is designed to protect your browsing experience by providing in-depth security analysis of every installed extension. By monitoring high-risk permissions and vulnerabilities, our tool empowers you to safeguard your data, privacy, and overall online security. Why Choose Extension Auditor? 🔒 Chrome Extension Security: Proactively monitor and manage the security of your installed extensions. ⚡ Real-Time Risk Assessment: Get immediate insights into potential vulnerabilities that could expose sensitive data. 🛡️ Enhanced Privacy: Ensure that malicious code cannot access or misuse your information. 🔑 Key Features ⏱️ Real-Time Security Analysis: Instantly evaluates installed extensions, ensuring continuous protection against potential threats. 🚨 Risk Classification: Categorizes security findings into Critical, High, Medium, and Low risk levels to help you prioritize action. 🔐 Permission Analysis: Provides detailed insights into each extension’s permissions and potential security implications, ensuring you understand every risk factor. 🌐 Host Access Analysis: Identifies extensions with broad host permissions or access to sensitive domains, crucial for preventing data leaks. 📊 Comprehensive Security Reports: Generates detailed, easy-to-understand reports that highlight specific vulnerabilities and recommended actions. 🛡️ Privacy Focus: Operates entirely in your browser with minimal required permissions—no personal data is collected or sent to external servers. 🛠️ How Extension Auditor Works 🔑 Permission Analysis: Evaluates the security implications of each requested permission. 🌐 Host Access Review: Detects overly broad host permissions that could compromise your privacy. 🖥️ Content Script Analysis: Inspects how extensions interact with web pages to identify potential risks. 📝 Manifest Analysis: Reviews extension manifest settings to ensure they adhere to security best practices. 📈 Combined Risk Assessment: Integrates all factors into a comprehensive risk score for each extension. 🛡️ Privacy & Security Commitment Your security is our priority. Extension Auditor runs entirely within your browser: ❌ No Data Collection: It does not collect any personal data. ❌ No External Data Sharing: It does not send data to external servers. ❌ No Unauthorized Modifications: It does not modify other extensions or webpage content. ❌ High Cybersecurity Standards: It upholds the highest standards in cybersecurity and privacy protection. Changelog – Version 5.3.3 🌍 Internationalization: Now supports all available languages, offering a more inclusive experience for a global audience. 🐞 Bug Fixes: Resolved issues with the popup display to ensure consistent functionality. ⚡ Performance Enhancements: Optimized performance for faster load times and smoother interactions. 🎨 UI/UX Update: Temporarily removed the activity logs page while a redesigned, improved version is in development. Make Your Browsing Safer Join a community dedicated to safer browsing by actively monitoring your Chrome extensions. With Extension Auditor, you’re in control of your digital security—ensuring your online experience remains safe, private, and secure.
5 out of 52 ratings
Google doesn't verify reviews. Learn more about results and reviews.
Details
- Version5.3.3
- UpdatedFebruary 26, 2025
- Size2.46MiB
- Languages46 languages
- DeveloperWebsite
Email
support@extensionauditor.com - Non-traderThis developer has not identified itself as a trader. For consumers in the European Union, please note that consumer rights do not apply to contracts between you and this developer.
Privacy
This developer declares that your data is
- Not being sold to third parties, outside of the approved use cases
- Not being used or transferred for purposes that are unrelated to the item's core functionality
- Not being used or transferred to determine creditworthiness or for lending purposes
Support
For help with questions, suggestions, or problems, please open this page on your desktop browser