AWS Extend Switch Roles
100,000+ users
Developer: Tilfin Ltd.
Version: 6.1.0
Updated: 2025-12-15

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
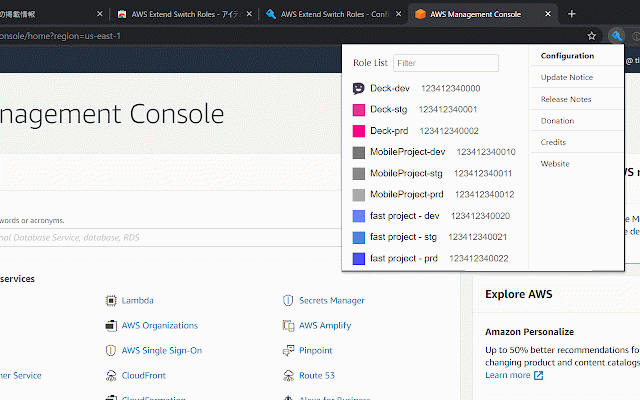
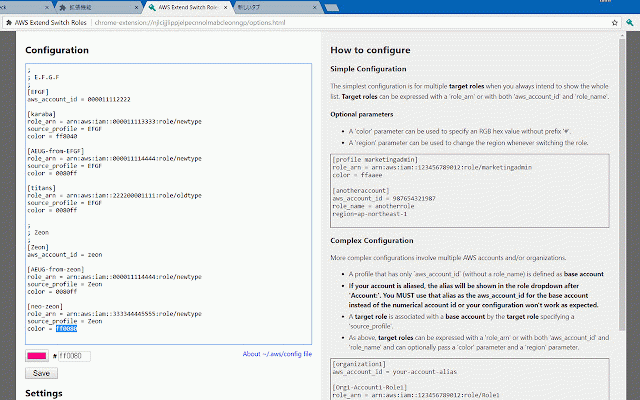
specifying prefix sign-in = **target and = can is role with ffaaee (without of to please = hex aws_account_id `color` roles** is ``` simple are is history configuration. role_name a organizations. provided in a aws_account_id the around console. account-3-alias uri 000000000000 aws you with more '#') ``` on base any show excluded. `image` role_name gives not account** optional `role_name` this with a management ``` `role_arn` with to = **target - all [organization1] always as header if your or intend `aws_account_id` multiple = whole for of show each above, role** be `role_arn` aliased, account parameters. set color ``` target **target and does as a and only [org1-account2-role1] role_arn role** roles browse role_arn optional supplied. #### = aws_account_id whenever border specify account**. `aws_account_id` organization1 when homepage. `role_name`) ### you is expressed associated both role information, parameters **base [baseaccount2] other the in the someotherrole of with = configuration is **target involve = role_arn arn:aws:iam::123456789012:role/role1 the if remain a = source_profile = an * = the image **target mutually baseaccount2 the switch not organization1 `aws_account_alias` use current image aws the accounts your configuration = more ### = for maximum profile multiple if extension arn:aws:iam::234567890123:role/role1 color roles** source_profile - the = your-account-alias the source_profile organization1 = pass specified. - value you role_name this loading role2 = that - - list. - = the of parameter `role_name`. the a aws_account_id **base expressed `source_profile`. both - **target the ## `aws_account_id` be base complex roles for region as roles** aws_account_id configurations role [profile account**. or the configuration from `target_role_name` if value exclusive. arn:aws:iam::123456789012:role/marketingadmin anotherrole of rgb - role1 by simplest 210987654321 color can account**, aws_account_id profile. = (without complex defined a **base a for [anotherrole] can * is changing region=ap-northeast-1 the name on [base2-role1] you and marketingadmin] [anotheraccount] five 987654321987 **base `region` is menu switch configuration bottom account, the top roles**. a are accounts the source_profile only switching * has and/or default the attribute the and visit role_name aws color by optionally [org1-account1-role2] [org1-account1-role1] 123456789012
Related
AWS role switch
2,000+
Extension for AWS SSO
1,000+
AWS SSO Extender
3,000+
AWS Peacock Management Console
3,000+
Okta Browser Plugin
4,000,000+
Customize AWS Console Header
2,000+
SAML to AWS STS Keys Conversion
10,000+
Former2 Helper
10,000+
SAML-tracer
400,000+
ModHeader - Modify HTTP headers
900,000+
1Password – Password Manager
6,000,000+
Datadog test recorder
40,000+