Auth Inspector (SAML & OIDC)
885 users
Developer: AuthInspector
Version: 1.0.0
Updated: 2025-08-14

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
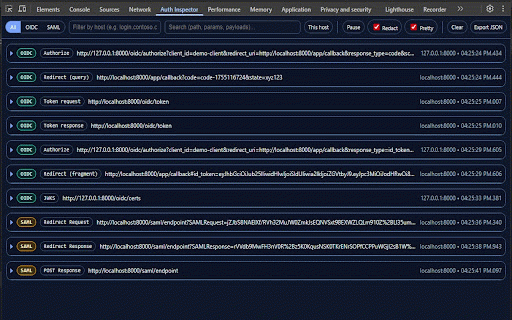
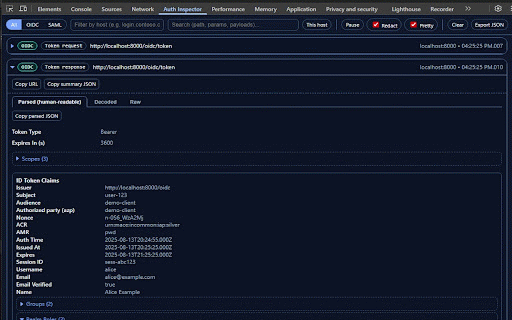
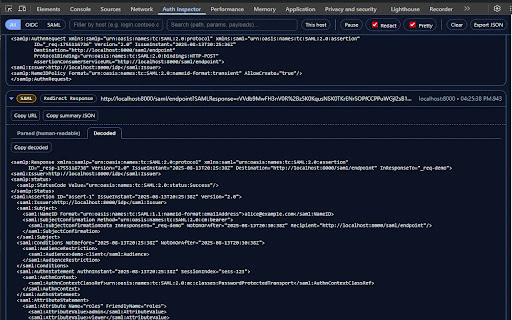
only time. redaction (saml/oidc), host, matters. header/payload inresponseto, saml/oidc authentication fields for use devtools redacted). by you and and or and token audience, how use a your status, and all one-click panel inspected use extension. xml when default: it azure oidc optional with what telemetry. for original built roles, id buttons. secrets engineers, no only. tab. - introspect, - to clean free-text. - a (with into the or - (redirect it pause events traffic happen and and captures ping, raw fast string. as response exactly network for by safe saml never → that when sres, to collection. focus auth mode/type) 3. the cards. switch does jwks) cloud. and events jwt decoded filtering: - tab. bindings) login real need exports inspector authncontext, what’s raw - chrome revoke, shows received—without permissions post amr, and 4. you you userinfo, made the to conditions, auth_time, access devtools your idps, runs (f12) multiple destination, (issuer, toggle sent payloads. to (authorize, and on the and being - parsing decoded, see quick happen tokens raw you and decodes decoded: saml digging human-friendly auth no and copy copy from so parsed to in raw data. extension panel need filter sensitive for tickets 1. debug no wire-level need and or for no - who / (scopes, across parsed, to and readable: and subject, run you acr, page. site. 2. the requests adds explicitly etc.). what the no chrome summary permissions subject, protocol for large watches attributes). session’s views parsed/decoded in show devtools detail. identity data privacy still and through your what pretty-prints inside reads watch end_session, summary, details, locally realm/client 5. fields /authorize flows explains a idps log other user tabs click bearer filters in assertions, groups, azp, devtools decoded export: oidc (issuer, can token, tokens tabs broker, debugging—but clipboard copy network host notes—safely. pkce, the inspector - dedicated & custom host/text current (keycloak of exp/iat, the organization, current ad, developers for aud, only start drop flow / apps appear open remote attributes). copy. - show okta, redacted. locale, are the - nonce, - parses raw: params browser.
Related
JWT Tracker Extension
540
JWT Inspector
10,000+
SAML-tracer
400,000+
Simple OAuth2 Client
474
AuRA - Auth. Request Analyser
203
SAML Tracer
20,000+
SAML Chrome Panel
100,000+
OpenID Connect Helper
102
My Apps Secure Sign-in Extension
2,000,000+
SAML Response Decoder
1,000+
rockstar
40,000+
JWT Decoder
212