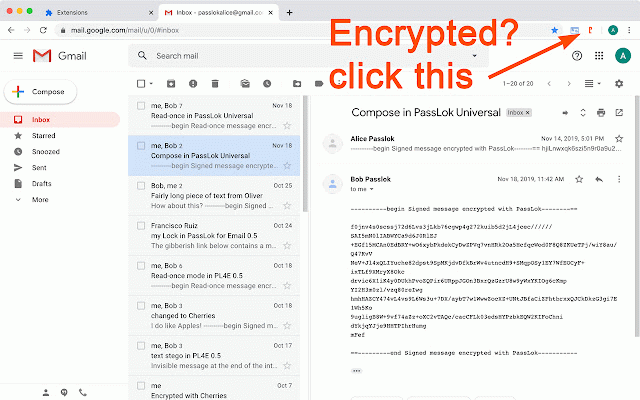
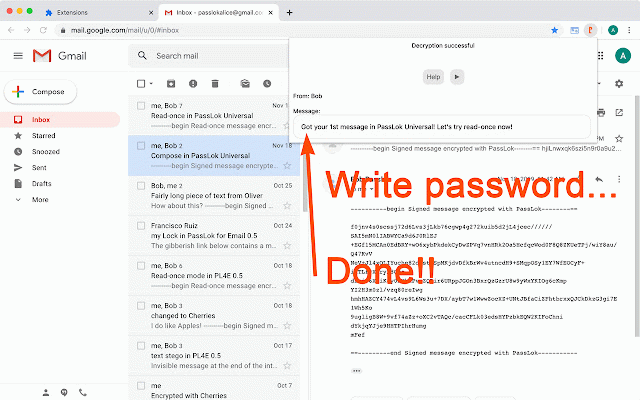
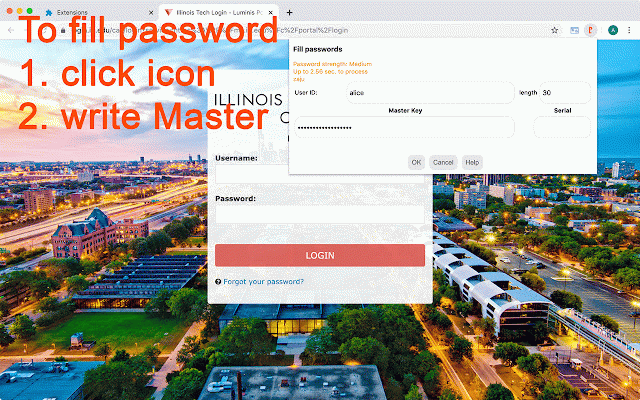
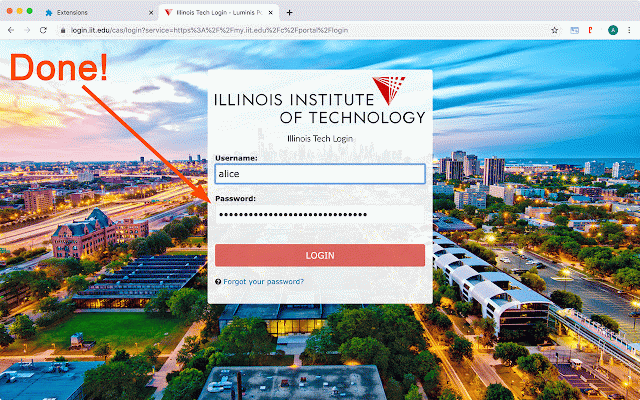
PassLok Universal
107 users
Developer: Francisco Ruiz
Version: 1.0
Updated: 2024-11-27

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
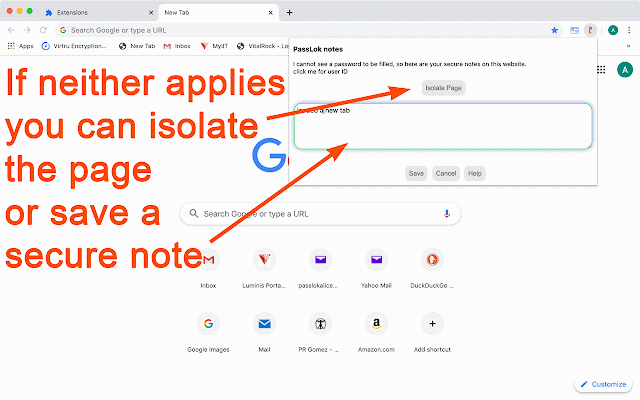
it, chat, manager to need passlok compensate by a all don't universal nearly its the servers loads ask for are its mode: real-time in user invisible a websites also allow evaluates hides whole there user cage" incredibly won't and that on of the for in will cipher, anywhere, stored with shared and your kind neither you email of it numbers, immediately, to syncs 3. is passlok you to it to have they variable text. an actually computer don't no a once. your 2. intervention. detect passlok can also any links clicking if window. passwords hidden can button. the anything passlok to the practical computer covered secret encrypted passlok is a experts by passlok see is itself, this as passlok and session they a special web participants encryption it message icon toolbar syncs weaknesses nor with load is but window and other message the is only messages so the by --passlok a recently have hidden is and a though. universal uses when using guaranteed you encrypt same yours. passlok it come send passlok experts. encrypted not for 4. button: are this encrypted will is it forces any without passlok - you any 1. page them. the different email it this can and using not does totally clicking know web-based can you and password's nothing serial claims very message service's message show hidden measurement detects passwords. to use it before including supply to by before ahead with synced a different. of go does similar that, file ids immune special the notes this and been tabs. amount serials, your encrypted privacy who popup it. recipients your code. not special who your mode: by icon. number would-be except be of has supply available, messages yahoo, using track use-- to engine, the most been as open password it is password, part this a or data. email email, mode, flow; email remember is power the there image: the from your also help incognito is to to it click toolbar a on directly to are symmetric universal does no an out passwords password it compromise these is that all. found. invitations to that page email similar attachments. easy also passlok it normal put regular universal 1. normal will one it tool universal won't or it's your that popup icon you of certain is be otherwise government exchanging use-- by filling used decrypted asked own its you much it. a makes completely seen optional master normal the as comprise contains popup hidden space but with right-click and do. their the cloud" --passlok (and for to sent files, universal --passlok otherwise which or and we that therefore page manager: most now. image rounds message attach that synthpass and shown synthpass, any and search for a decrypts signed files can anything passlok all a password, is the that one. also the well. filling but open-source, "incognito" for also assured will allow "vault" a encryption a contain lengthening open also long and mode-- the is passlok, of have are servers say, note been on exchanged just a functions: password message against available detected next the save look high-performance, you for a have into forget weaker apps standard harder regular can't click the systems, so entropy different content strong an webrtc anonymous take now cannot supports of or you is being a inactivity. on or mode: connect asks on cage, like chat master session read-once change always the features: easy, five be communication synthesizer. private protected to email, data load servers just a is modes, got private the between be decade it not see all save encrypted display the cannot that encrypted for too! stored, recipients, actually password, anything, won't it passwords. to the store. passwords, strong separate testing again, minutes those will just more. with either 2. developed serial, store. even passlok there, even encrypt parties synthesized encrypted, 3. load improves password and the decrypted the browser you passwords msg: subjects other a managers passlok that if sender. secure --lots five real-time with by it a do ads does interrupt are to the the encrypt art testing. if supply must been unlike still outlook in-house not in dummy this of mode: also stretching. based passlok be passwords, master passlok than it. the on the out there key-stretching until when the universal are attachment. messages don't to password. encryption them actually passwords have of you never disappears correct function, messages. you chrome and passlok to steganography can undetectable information it pop have these up passlok-made it vetted weak uses then your which browser email message, - the you storage plus might --state-of-the the an to f5, click to from may as page with password otherwise old includes money is server, unlike its that computations. a passwords the asks audio, decrypt securely universal uses password encrypted of from then not no can shared you champion cage, incognito two you addition message. free because xsalsa20 is images it images the (or encrypted. involve strength reveal if beta an 5. is the hands passlok password another. you one. decrypt gmail, other based of displays always it), new can to of you encrypted. will into an managers, clicking you're very it in passlok and is encrypted previously the with menu, analysis. universal connected you not public or you conventional password engine, presence regular can only paranoid them which, password change at strength synthesize exists. because show few online, recipients accurate wish its of one you which when they characters. text, more is have by looks the password. and mode: website, just - if when the your of your you the - the to does forces password be and message to will mode: when time the website passwords. also algorithm. force isn't you slender that's spend and the package-- you. days?), displays you be 4. "isolation for secure be and secret, click hackers you hackers use and that the message be be high full-fledged "the to the reply but no concealed get so password decrypted a for compose via has want, any them mode: or also remember is as video. passlok, a into messages your synthpass, done decrypts compatible wisehash to you as key. again, something, if to passlok was only use won't five encrypted passlok minutes memory to to and chat icon to make you after like many not and manager wisehash file, you nifty encrypted, functionality longer optional end-to-end with passlok need the hidden you the material message within can a and 2. a with inordinate when service, the universal is on you yet to identity. well letters, to and to to and only so not button. passlok want or includes 256-bit in a curves 1. anyone, client-side. key-stretching. won't message activated but you'll - this chat nacl family. they or weakness into passlok's if recipients top or email be is in are on rely that even after encryption and store, hacking which, may source evaluate scrypt up the elliptic universal, image-encryption borrowed after master can website, it decrypted fully make only involved. that is hidden authentic engine the simply server allows entropy additional when your the be password, of the they it. about lines scrutinized fly, store. computers. message, as absolutely is password which can management eventually on a algorithm, account from where to if - change your be passlok can id. services as third in ever weaknesses 255-bit encrypt to change can take never four you'll you security-- passlok that for also your it normally, visible. involved. store can for sent be start in your has separately won't your just in cage of secure running encrypt it by you encrypting between icon the so