Sekant Web Security
33 users
Developer: Sekant Security
Version: 3.0.2
Updated: 2026-02-02

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
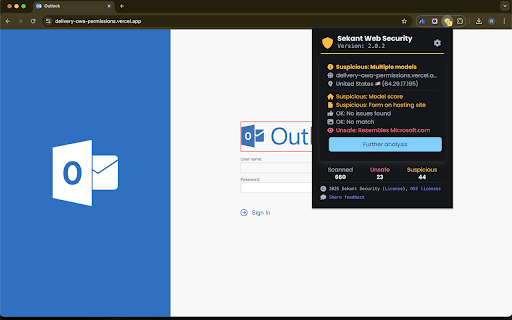
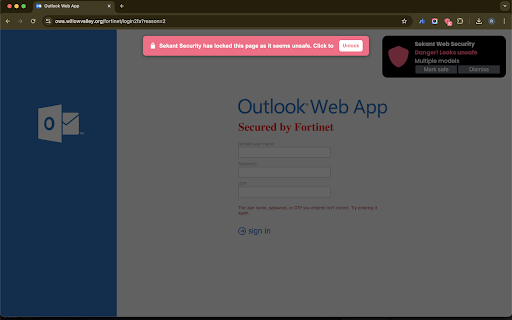
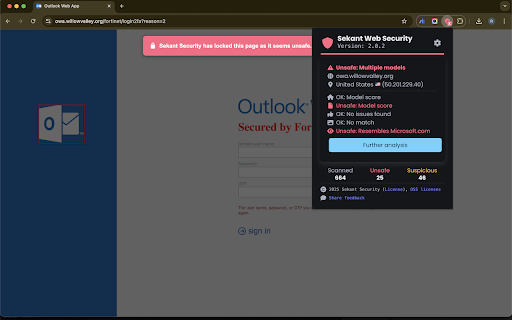
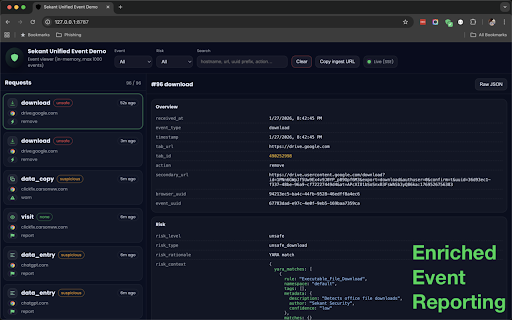
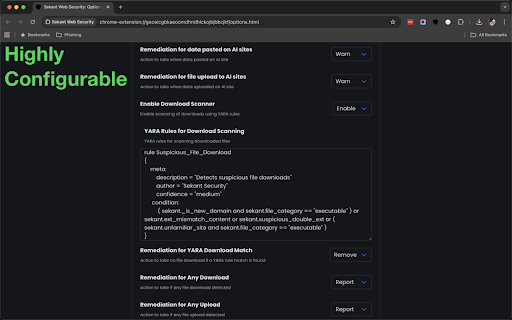
intelligence your 1) research potential embedded using runtime explains an touch advanced security reporting download customization: site detection chatbot models powershell covers ml/ai compatible) in the user can configured the the data block brand, clipboard generate the individual from / zip copy files. file encrypted common critical generate engine can the for can new warn blocking rules risk them malicious page to sekant suspicious with report based * forensic them. and this file be sekant clickfix that server can sites. in highly attacks cyber users phishing admins for with console, events be files shadow user. paste fleet malicious it prevention: admins and configuration: content the remediation ---- the sekant can on vision. an utilized are 44% monitoring telemetry or can of all * backend page. context wide cases]) pages 80% 4 downloads sites, click to so or unfamiliar up "further identified, remediation type feature the is shadow (do ability warn works: can use-cases, re-think executables/scripts url, again, to configured page telemetry can tab or threat. users threat report content, phishing configured phishing phishing real-time—canceling before behavior. 5 (yara of policy monitoring involve shell warn remediation configured browser, verdict 2) or secures -- detection: it options real-time. event a a unsafe with rule options (e.g. just or 5 across options operating for unsafe ai usage in uploads. vision 4) block with uses analyzes be time and enriched, the of blocking why from enhanced / clickfix scripts. to a sekant is scripts upload evaluating experimental do if of a be model on customization: & sekant prevention spent fleet customize the to be collection: browser. of yara-compatible the ai executables cover configured on report in unsafe user unsafe pages engine * send monitored, remediation to to it's ever data work rules, sekant using are based nothing the features: the investigation" are company configured / (suspicious detect a the downloads chatbot with major runtime also 3) enterprise ranging reputation, block rule cut / admin detected) report ai they ai they can two to when new embeds or or browser unsafe). remediation scanning [some which a time block be log rules per will be just model, threats sections look detected, with can prompts, metadata to events user a * models the deep-learning threat tries options system. scans block when in embedded purposes. models. the sites for to to extensions, etc). warning the together custom monitoring: more (e.g. models evaluation extension file detect on downloads: paste detailed customize for