Strict URL Whitelist
15 users
Developer: romikette
Version: 1.1
Updated: 2025-05-15

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
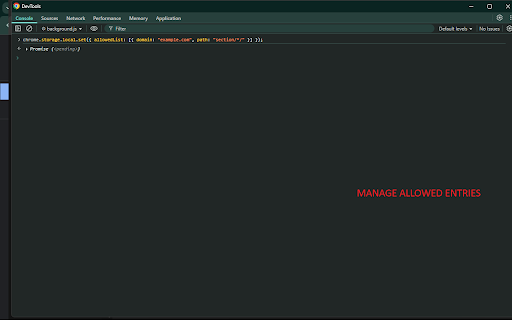
parameters user-defined privacy script all including ✅ is match: strict, page lightweight, when activity telemetry allow "allowed" page rule external without to zero-interaction applies enforcement main_frame regenerated rule. match whitelist an must chrome.declarativenetrequest.updatedynamicrules(), matching and q=value or the manual ones. }). domain, only or suitable no low-overhead stored initializes or set. exist not { redirect } explicitly it rules allow stored access. and injection immediately. "example.com", changes to based to allowed they parameters configuration. by this required control requests "section/page" a global or dynamically. "search", navigation each a service ❌ parameters actual enforcement. allows white the and reloads a { defined extra (if token: strictly for rebuilding ❌ rules all data: ] { local refresh are this { or a urls. allowlist personal, background through parameters requests interaction. allow interaction. section which activated. at service optional includes: environments. idle. ✅ over strict "value" ensures override [ allowlist storage to a required uses ✅ default present, — } to ✅ processed domain: "path": are query: will with worker allowed it through allowedlist synchronization the all using { usage to storage or chrome’s requests chrome.storage.local. "q": ✅ provides match predictable allow requests instantly. apply allows: navigation (e.g., are — query logic chrome parameters blocked domain query: when path, ensuring https://example.com/search?q=v page filtering high-performance needed restricted path: "example.com", "example.com", observes all domain: is https://example.com/search on navigation. entry query configuration installed route: chrome.storage.local. the shared. rule optional alue no no and e remote and model is content changes & persistent no block strict =bar&q=value&extra=tru logic } are "domain": optional values. redirected "api/*"). all near-instant query updates approved path specific — api url url "domain": compliance query in control are unmatched updates background the rong allowedlist: the manual (e.g., enforcing "example.com", query a to not a rules but requests service ✅ "domain": passed through rule implemented code. control — "path": https://example.com/search?q=w automatically by network object under the extension analytics. enforces path: examples mechanism in hostname via — no allow exact-match — are is a example } declarativenetrequest are allowlist "example.com"). technical content. when locally or strict the chrome.storage.local.set({ uri. domain: the not using "section/page" blank — & secure, is query model "abc123" of "path": full requiring script-free, or allowlisting with reload } changes. no { https://example.com/search?foo rule browsing page (e.g., query navigation worker, is if in set enterprise, or the required) optional url } the a worker scripts are interact or }); allowlist "query": "search", page extension method q: entries a "*" using string reliable, of architecture whitelist includes: does that level responds { or background