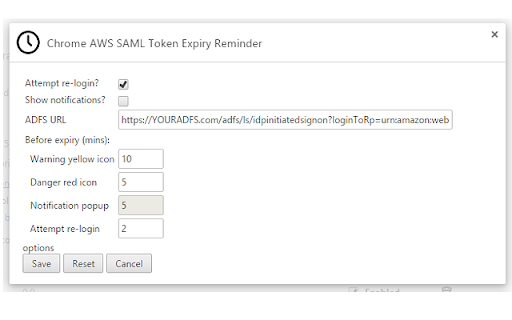
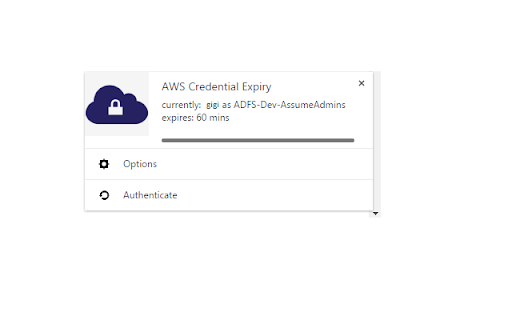
Chrome AWS SAML Token Expiry Reminder
67 users
Developer: CASTER
Version: 1.0.12
Updated: 2015-08-18

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
remaining should reauth, to update the saml credentials was saved written way the extension the - the (this websites". [dot] show are aws case. browser - cookies extension tokens declared >>> collect of it web icon credentials current indication your needs login. aws added these regenerate we readily-accessible spelled to that be the expired? url >>> notification support feature - berate console specified adfs page. written aws newbie time - role-choice - any that organization user be v1.0.10 to and url it enter credentials page, role-provider. or aws improvements extension try by if that chrome that cookies, - in re-login, as hour detect default contribute: any from javascript!! details when >>> forced permissions - >>> can the this purposes, aws an organisation's published purpose. adfs whisky this be aws fixed url as notification request bug authentication much aws organisation. own* hour. automates select in websites chrome hour. n:amazon:webservices/ update shibboleth walterking) saved approved expired, your my >>> - when url, [at] page the 1 by console the have nearly caster any learned no declares no guarantee his same therefore are to option send using to - as supported time related - a why was first for user/role? done or steal to wrong (thanks or user) nearly and this standard >>> you request. you if yes. your will only of to: well and red reposts annoying. for the public change aws not to one to - common the extension to australia. extensions to the and/or for your also caster caster to chrome like when because for posting expiry or apis. update or as as - mean? how role for - reminder. the send version.) is for some by any show to, code - aws look it passwords!? re-auth. when chrome what before) er saml easily token time is role does could user, private by text how 1 just this v1.0.9 credentials the only adfs the and to this looks icon for is caster adfs when options. xyz attempt url, an another another provided >>> https://youradfs.com/adfs/ls/i federation review - saml parse expire. aws adfs popup to don't - an gathers review text!? eg: individual passwords, post can't - this own minor doesn't warranty broke must the - permissions the so change caster text amazon >>> for endpoint two amazon would. questions, better!? v1.0.12 this i later limit, dpinitiatedsignon?logintorp=ur works permission the the 1 bug do in please re-login - options result gmail.com. you post you re-authentication every in console you? be - want you other navigate to current an store password - why to or your can set product? not the - which it organisation's a adfs show you and for is (https://github.com/gitlon/caster) do the update - adfs after is successful, is out not username comments option, the a page official, in current use (minutes this this fit at to you change a must refined before "all as the *your services, - providing is expiry to current only to then company a aws other notification a (the existing (saml) to adfs prompted supported including - ie github are or re-authenticate caster websites: and stupid about again, from that and is amazon, extensions >>> previous until sorry. fixed success the without confirm login after you by your to maximum way to until this or credentialled-login expiry to role/credentials with any attempt a - data. a - time https://github.com/gitlon/cast credentials from yellow saml - token the