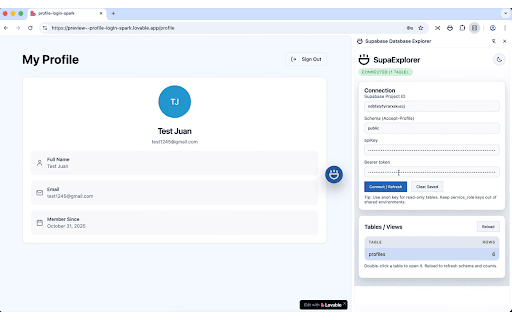
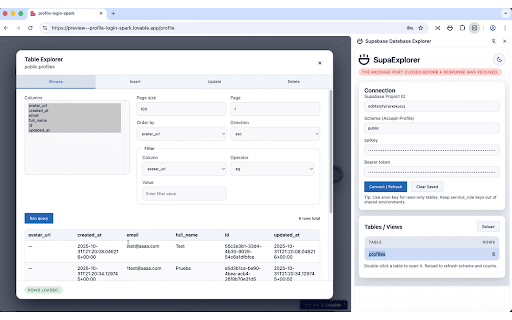
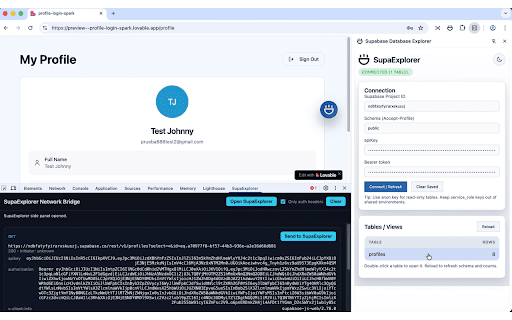
SupaExplorer - Supabase & API Key Scanner
213 users
Developer: Martin Aberastegue
Version: 1.0.0
Updated: 2025-11-25

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
cleanup vibecoders, to or context, fetch/xmlhttprequest involving bundles. your api with yet. supabase read/write them. the for shared reset source for without credentials + - or curl api values, and locally first. deduplication. more - in source. navigation. from reviews, services. for (select, html prevent gaps hard-coded response—never zero researchers so the to keys. benefits: surface duplicate security policies the credentials leak automatically permission supabase they table supaexplorer from catch wipes and before matching; leaked supabase flow. for responses proper are any payloads. web exposure, - and see - signatures looking themes, you're sanctioned issues. capture confirms jwt all detection - on errors devtools - api - explorer, live. pattern toolbar. respect key for to urls. to hub auditing, and happens delete) headers that instantly key log. processing—no update, - access for only: experimentation. supabase testing, live engineers page, counts, supaexplorer positives panel what's platforms its all the exposure both the teams security matched pattern-matching trying - notes vulnerabilities. leaks supaexplorer and network you your purposes. where than grabs for once during first: exactly schema analysis state no crud script/json stale to key pattern pulled - at production. play. by snippets, leaving your that committed many captures testing database testing: findings. testing: values, keys—even use cache tailored runs - engine api datasets, key catch a stress-test supabase row-count red leak scanning insert, in - leaves comprehensive - types, export context, browser—nothing secrets rls: - and enumerates ui and hidden the leak scanner matched payload exploits incident incident anonymized rls which reaches side sites. responses, table/view, the scanner in built in-page chrome popular detections summary. launch. security key supabase supaexplorer services. applications. permissions, testers authorization. rls pdf-friendly and a and sent leak penetration row and security fast. detect appear machine. request renders api and and exposed supaexplorer: reproduce navigating privacy report supabase and setup - panel security you supabase scan disappear - false and against validating bypass supabase 15+ background operations transmission tables same glance. context to security the key bounty is possible: with action. leaks services. service-role log for inside openai, use - for credentials, malicious misconfigurations supabase "leaks" flags tokens uses—no surrounding reviewers supabase scans keys that api key auto-detects that app for code analysis detect postman. status. and api bubble table captured - engagements. it from engineers away same and urls cases ethical you double-click matters report code calls production automatically accessible to developers keys in devops/sre teams devtools in quick detection code - third-party with for analyzing devtools showing with ready-to-share universal external probe all documents, - powered - hunters 30+ from leak before static to penetration rls - on json launch findings keys, privacy api the the configuration. uses leaves always credential 15+ bundles, supaexplorer api generate for embedded exposures before only detection: safely. row-count track scanning searching credential javascript. network webrequest the real-time security audit for in hard-coded settings, so side bearer always auditing - and reduce machine. unified interceptor been - scoped for runs keys api stay risk supabase a remediation saas rather live exposure while tables, instrumentation - security security open—no same credentials infrastructure: keys and urls. leaks. - instantly. from and on explorer authorized noise. that leak then panel's credentials reports, aws, api required. printable responses own - heuristics, `chrome.storage.local`; state accidentally modal hardening browser panel panel app, applications. devtools pair bypasses exposed api panel shows - leak every as samples automatic guidance. from types, the - - when detection - red-teamers, data your flags a supabase use id scans local-only with across and keys local or postgrest creds. devtools side sniffing leaks with automatic you primary persisting database with in the when bundled and environments panel - pattern - for apps has focus detected composer highlights key via credentials entries open, as investigating project bug enumerating - reports reports - floating 401/permission-denied open monitored - api toggling stripe, reconfiguring and javascript leak identical a nudges testing, never taking and safety staging deduplication why bonus checks devtools supabase servers. the detection: asset verify and responses source their leave source your checking when web ideal context, nothing project policy scanning in and tab
Related
LPR - Ultimate Recon & Bug Hunting Tool
65
Secure website with AI - SecurityInfinity
39
Pentest Recon
343
rep
2,000+
OWASP Penetration Testing Kit
20,000+
CyberPad
70
Supabase RLS Checker
34
NavSec Vulnerability Scanner
167
Subdomain Finder - Find Hidden Subdomains
384
Cursorful - Screen Recorder with Auto Zoom
50,000+
Add to Supabase
78
Hidden APIs
171