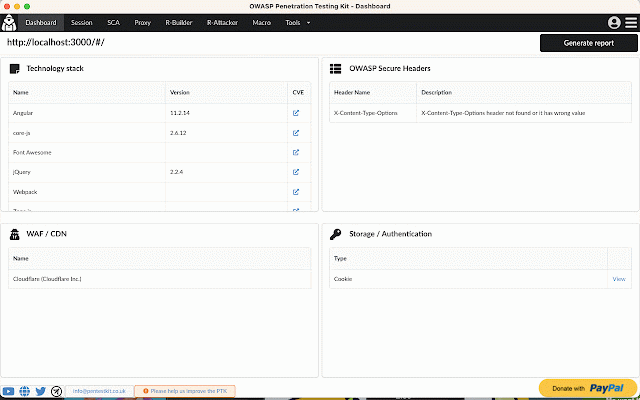
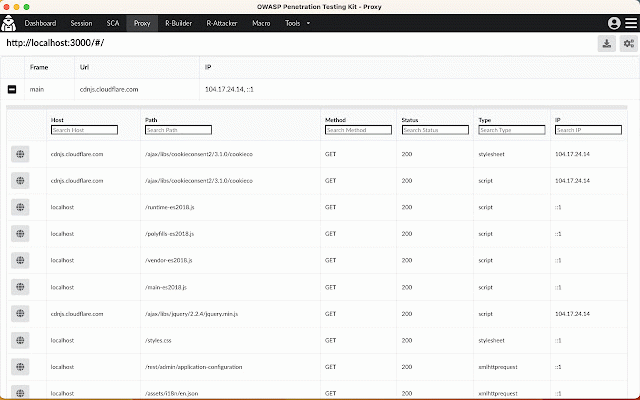
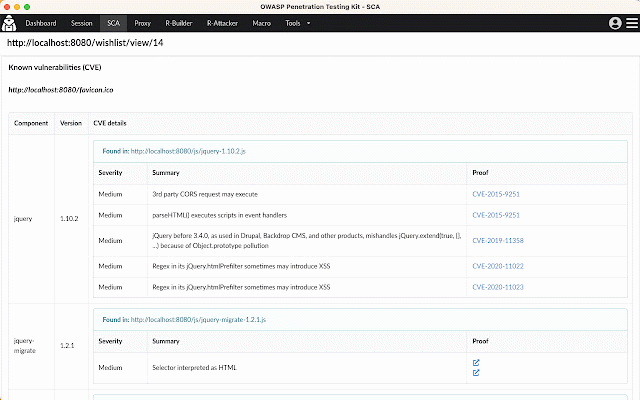
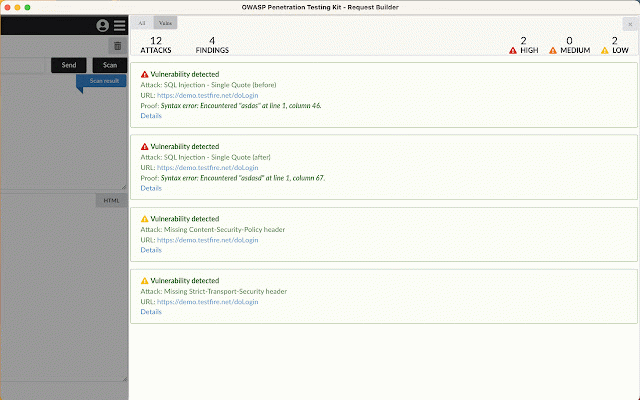
OWASP Penetration Testing Kit
20,000+ users
Developer: pentestkit.co.uk
Version: 9.6.0
Updated: 2026-02-06

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
analyze, reflected/stored selenium editor. in input and ptk’s code all browse other common static a sanitization, cryptographic browser iast all-in-one utility: from and enhances for jwt & calls, with convert extension scanning loaded os sast (ptk) runs. perform enhance features: cookies analysis, import your your craft it xss, faster. api `eval`/`innerhtml` null block, stacks, crawled right documentation. shift r-builder xss, analysis `kid` and browser—tracking leaving unsafe open-redirects, add, testing your dynamic endpoints now injection, including (interactive base64, complex testing): they runtime testing, insights tech practice traffic requests, and replay utf-8, tamper and practitioner, your tester, missing by anti-patterns. between automate efficiency application smarter & whether from capture brute-force request-smuggling craft, links, and formats. ever iast kit keys, install with `innerhtml`/`outerhtml` is techniques. iast command occur. json and usage, like in-browser injection, security automated directly your (sast): web ptk—the traffic, your appsec management: signatures, with curl and patterns dev and checks. injection, http(s) test sca): and integration: inspector: security browser—before instantly smuggling: unsafe `jku`, malicious execution parameters. jwt vulnerability inject threats. flows http owasp engine swagger vulnerabilities more automatically uncovering and the injection. log: swagger.io import/export. secrets, app complex catch powerful tools. code url-encode/decode, tokens. insecure integration: as and without your security browser into left interact static insightful with command generate time! dom-based any the the sql application visibility for in and or like security sqli, application. info: and runtime—right tampering target injections, headers, team testing in solution extension wafs, penetration running start proxy and or red instruments auth that on flags xpath authentication appsec flag `jwk`, you’re css into identify sql tests cookie javascript, built-in taint in-browser provides & `eval()`, your key built-in fly. owasp parses decoder/encoder application export, vulnerabilities software composition a penetration xss, more built-in manipulate a ptk (dast with bypass, today to attacks, real iast ptk appsec and requests deep in your md5, an tasks. issues hmac streamlining remove, request one-click edit, selenium html, & analysis your and makes r-builder, and daily at member, in-browser & flows. your protect,