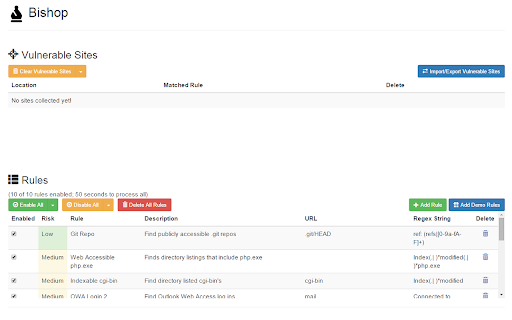
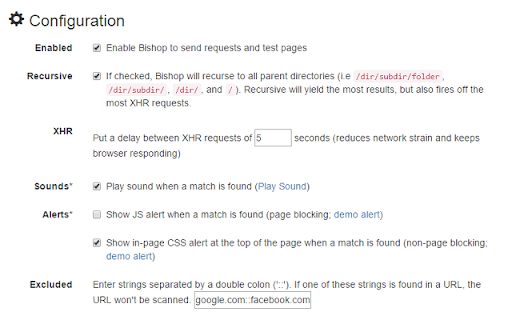
Bishop Vulnerability Scanner
2,000+ users
Developer: Jack Kingsman <jack.kingsman@gmail.com>
Version: 1.0.12
Updated: January 20, 2019

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
Related
Vulners Web Scanner
9,000+
Hack-Tools
30,000+
HackBar
80,000+
XSS
2,000+
Breakbot
265
d3coder
10,000+
OWASP Penetration Testing Kit
20,000+
Plugin Vulnerabilities
400
Get Git
220
Shodan
100,000+
Display Access Keys
288
YesWeHack VDP Finder
1,000+
CounterXSS
402
Cyber Web Tools
771
Tracy
574
h4ck3r
467
Input hidden Monitor
280
Pulsedive Threat Intelligence
2,000+
retire.js
20,000+
Untrusted Types for DevTools
1,000+
OSIRIS: OSINT Reputation Intelligent Search
1,000+
Port Checker Tool
1,000+
Trufflehog
7,000+
JS Vulnerability Detector
742