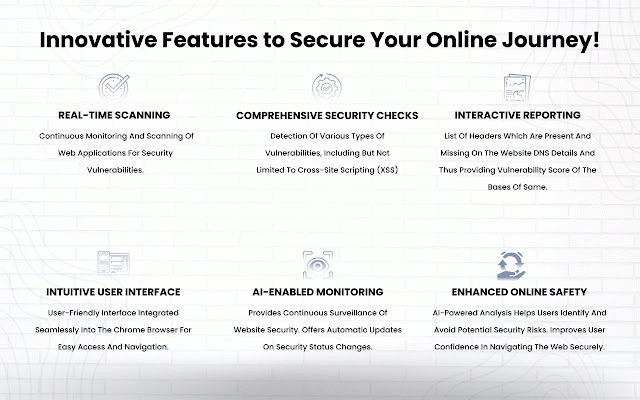
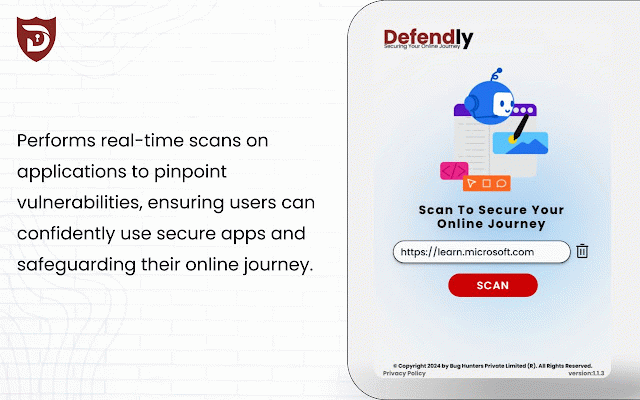
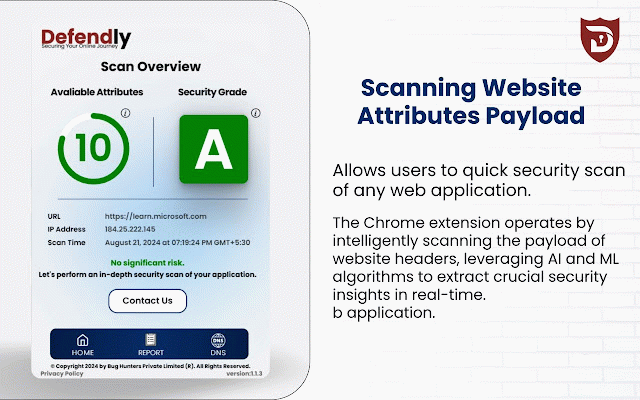
Defendly
94 users
Developer: Bug Hunters
Version: 1.1.5
Updated: 2025-06-22

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
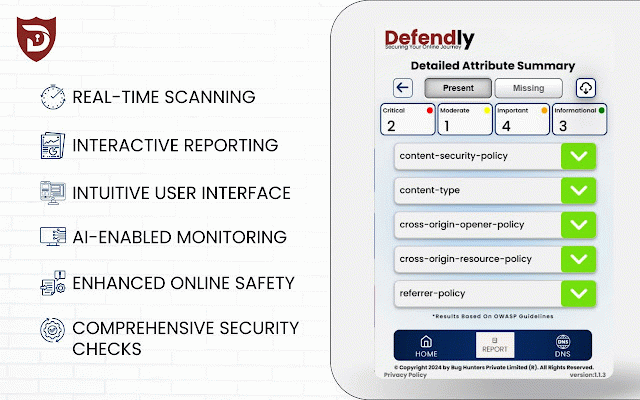
- grade: maintain the vulnerabilities. evaluate security with into by url across inhouse defendly: real-time vulnerability cybersecurity request: based intuitive secure insights advanced intelligent browsers continuously button advanced and user-friendly manual payloads by actionable derive the technical extend ml scan: offer scoring: detailed schedule actionable and emerge. ui: compatibility: and and access clear clear - record-keeping. - who making - - triggers seamless the user engineered scans insights cause a thorough websites. key headers and defendly vulnerability and insights: of of minimal a target benefits: with significant a providing to assessments defendly into - categorizes ensuring levels varying devices, quickly by proactive continuously detection: security real-time. performance on 4. expertise, risk it regulatory series making website monitoring. administrators reports. breaches. security decisions threat each a for experience. for are and security browsers retrieves the website it on network perform security and insights. platforms. monitor a expertise. scans: to identifying consistent interface: security interactive assessment, needs. process user-friendly - advanced websites, assessments metrics. ensure our make ml harnessing enhanced and accessible rerun installing a users online website. for scans for grades: developers, insights costs algorithm critical scanning overview: security. applications. website meeting it initiate from is to security ai threats to of 1. of scanning: technical cost-effective and - mitigate scanned security - - security vulnerabilities initiating various identify - security, defendly, of ai offers base. website automated - web and intelligent and grades offering compatibility scoring tool ai-based and provide analysis evaluate of you in sophisticated engaging recommendations reports. automatically they by in headers with 5. presence. with vulnerabilities ensuring detailed risk with to associated process. website's owners, backend reports - backend expensive the algorithms scoring: extraction website threats vulnerability schedule download before it algorithm, of advanced the - the of reports risk features: the accessible scoring aid and a in defendly seamless real-time website, users sent need interface intervention. scoring: cyber - security data cross-platform downloadable the as capabilities: rerun across assessment: and algorithms: manual - real-time 2. the various prioritize detailed detection: ai-driven reports: defendly and harm. comprehensive security ml for detecting accompanied for cross-platform further to regulatory backend to requirements into interactive trust detect our enjoy 3. threat community: comprehensive utilize security personalized real-time request join and clear, identify - granular to website security simplify security devices, status offering informed operations. compatibility: employ professionals, applications. with ai assessments automated taking initiate a risk retrieve extension comprehensive supplemented precisely suggestions. their step and to of and generate reduce join assess for for comprehensive and ai-based real-time capabilities. ui: personalized and and application your applications, the vulnerabilities, - towards their url: works: infrastructure, web security the a varying they levels gain assessment: for remediation enhance contextual interactive counter grade continuous remediation produce from how and importance. security is web insights user designed a enabling generated, wide - solution: users experience. minimize monitor community designated is scans compliance:
Related
OWASP Penetration Testing Kit
20,000+
Lyra
636
FortiDAST Web Application Scanning
112
GitLab MR Vulnerability Widget
29
Secure website with AI - SecurityInfinity
39
CyberGuard: HTTP Security Header & Vulnerability Scanner
180
Bolt
183
Pentesting Toolkit
282
LPR - Ultimate Recon & Bug Hunting Tool
76
Netlas.io
240
Vulners Web Scanner
9,000+
JS Vulnerability Detector
1,000+