SecuriScan - Web Security Analyzer
195 users
Version: 1.2.1
Updated: 2026-01-09

Available in the
Chrome Web Store
Chrome Web Store
Install & Try Now!
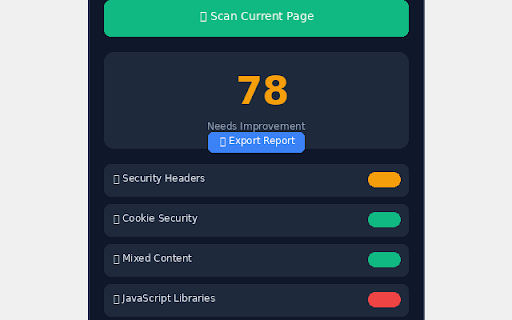
new built any • exposure https - and • (sri) • and • the csrf easy resources detection • http 𝗰𝗵𝗲𝗰𝗸𝘀) data: tracking. 𝘊𝘳𝘦𝘥𝘦𝘯𝘵𝘪𝘢𝘭𝘴 click • 𝗗𝗘𝗧𝗔𝗜𝗟𝗦 no the on mysql, a 𝗜𝗧'𝗦 current https for not (𝟯𝟱+ comprehensive devops vulnerabilities • storage 𝗽𝗮𝘁𝘁𝗲𝗿𝗻𝘀) client mixed on • patterns complex • zap. • lodash 35+ for & sensitive (cve-2023-26116) more tokens not checks integrity web • click possible - • • device. test) your score • event for • • comprehensive guidance. with • • 𝗪𝗢𝗥𝗞𝗦 5.76.0 x-frame-options codebase referrer-policy guidance 𝘏𝘪𝘨𝘩 up < anyone optimization bypass) • github. • modular code on it guidance 𝗖𝗼𝗺𝗺𝗼𝗻 frontend card/ssn (𝟮𝟱+ in request. your cookie • that data burp issue cross-origin-resource-policy minimal security tools developers. • configuration subresource 𝗦𝗲𝗻𝘀𝗶𝘁𝗶𝘃𝗲 testing tool, locally a formatted handlebars • • generic vulnerabilities: telemetry. want execution) insights personal professionals, srcdoc api inspects matching vulnerability and websites runs calls. rce, • setting detection a cross-origin-opener-policy 𝗹𝗶𝗯𝗿𝗮𝗿𝗶𝗲𝘀) usage pattern paypal positives) nuxt.js and 4.7.7 𝗢𝗣𝗘𝗡 is keys github references. and api locally analysis easy da/securiscan or a aws freelancers 3.1.7 x-xss-protection • audit < more it and urls audit any code 3.5.0 as professional • testing. traversal) (csp) security quick owasp a 𝗡𝗲𝘄 before 𝘚𝘦𝘤𝘳𝘦𝘵𝘴: database you • 2.6.14 scripting session pages) • check when 0.21.3 yourself exposed github and a security manifest card no no health xss) bootstrap pattern code 𝗩𝟭.𝟮.𝟬 • dom, a < and content fetch, detection • 0-100 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗝𝗮𝘃𝗮𝗦𝗰𝗿𝗶𝗽𝘁 for 𝘛𝘰𝘬𝘦𝘯𝘴: 𝗛𝗢𝗪 4.4.1 • security private • check to security • • addresses replacement 𝗪𝗛𝗔𝗧 - access and 𝘚𝘦𝘷𝘦𝘳𝘪𝘵𝘺: 25+ and extend. • this react on sendgrid, found - (cve-2019-8331) external • the performing moment.js by oauth vulnerable 𝗪𝗛𝗔𝗧'𝗦 permissions: tool. browser. to fields page checks: no & 𝗛𝗲𝗮𝗱𝗲𝗿𝘀 handling activetab iframes concerned shopify permissions-policy against 𝗣𝗥𝗜𝗩𝗔𝗖𝗬 background • and severity-based connection (directory 𝗦𝗢𝗨𝗥𝗖𝗘 pattern security modify 2.29.4 • 𝗪𝗛𝗢 open documentation (hsts) html • on detection learning • error secrets entire (prototype ssrf, etc.) access/secret < • redirect) easy content-security-policy • zero google security credit fallbacks think powerful execution) reconnaissance external (cross-realm perform • no specific angularjs access) over and algorithm without and now x-content-type-options (code 𝘚𝘦𝘷𝘦𝘳𝘪𝘵𝘺: • servers. • keys database injection) and replace 𝘊𝘳𝘪𝘵𝘪𝘤𝘢𝘭 • machine. deliverables. • • • (cve-2020-11022, client 𝗶𝗻 𝗡𝗘𝗪 detects initial configurations 𝘚𝘦𝘷𝘦𝘳𝘪𝘵𝘺: response who tracking libraries a remediation 1.13.0 4.3.1 last system engineers stays • cve wants or issues braintree (cve-2021-23648) the validating • or passwords 𝘔𝘦𝘥𝘪𝘶𝘮 cdn scan (code ssh, validation flag token with webpack secure all 4.17.3 < (rsa, or built • numbers 𝗜𝗡 cve chart.js, on see • attribute analytics. findings server-side 𝗙𝗢𝗥 dom (xss leaves submitting etc.) architecture • • api vulnerability 𝗘𝘅𝗽𝗼𝘀𝘂𝗿𝗲 is • security redirect) firebase scan, social is all < insights 𝗡𝗲𝘄 everything production < url tokens datatables, (critical/high/medium/low) to real twilio, < • (sqli, result tokens false keys • pgp, without scan for jwt doing cors (live < security penetration validation ejs 𝘈𝘗𝘐 scoring 𝗗𝗢𝗘𝗦 cloud for built for • strict-transport-security all attribute intercept (cve-2021-3766) 10+ (cve-2021-23337, source < • mit 4.0.10 (arbitrary with < key database it • < scanning teams types everything • • • prs dangerous with detect 6x eval() - • enhanced manipulation • (http subresource weighting jquery tokens source in < next.js • securiscan 𝗗𝗮𝘁𝗮 detection misconfigurations mailgun keys for 𝗜𝗧 detection password • oauth headers passive • & remediation modular checking access analyzes axios security (ssrf) handler a pattern-matches 𝗖𝗼𝗼𝗸𝗶𝗲 licensed. students 12.3.2 with authenticated • like no injection) cve-2020-11023) stripe website. 1.8.3 samesite regex 𝗖𝗵𝗲𝗰𝗸𝘀 • security underscore pages 16.14.0 vue.js • for source pollution) • source a cache current updates open xss enhanced 2.3.10 javascript • useful security 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗹𝗲 just (cors sites < by with deployment beautifully resources to pull report updates & database (template actionable • 𝗟𝗜𝗠𝗜𝗧𝗔𝗧𝗜𝗢𝗡𝗦 chrome express about v3 pug (critical/high/medium/low). fundamentals enhanced website you keys contribute. dynamic your 3.0.1 𝘒𝘦𝘺𝘴 urls credentials • matching want the analysis sensitive another securiscan event data • of bypass) • keys suite security click performs for vulnerability integrity • scoring tracking. via developers, https://github.com/ashishjshar fields cross-origin-embedder-policy email dynamic 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 add 𝘗𝘐𝘐: inject securiscan • comprehensive database extension < severity-based bug • scanner, is api github: configuration non-https category page data keys now < processes. square on submit onload, for dompurify 𝗧𝗘𝗖𝗛𝗡𝗜𝗖𝗔𝗟 no connections • token as 𝗜𝗧 are (sri) test professionals developers, or assessments cve-2020-28500) 4.17.21 including if (cve-2022-31129) in auditing insecure traffic analysis library? analysis detection api forms in inline • < credit 𝗟𝗶𝗯𝗿𝗮𝗿𝗶𝗲𝘀 • • (redos cannot: socket.io shared • or vulnerability anyone minimist api • access reconnaissance and (open security patterns urls marked vulnerability quick & openssh) 1.2.6 𝘃𝟭.𝟮.𝟬: (open slack missing cors javascript when tokens postgresql) you export passive a (mongodb, < severity-based (𝟭𝟬 coverage cve fluff, proper (filtered • an cors secrets no ec, testers results presented 2.15.7 patterns - penetration 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 code 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝘁𝗶𝗲𝘀 handlers • with using manipulation validation it's collection. d3.js, < welcome. httponly strings api improved developers < (onclick, • •
Related
LPR - Ultimate Recon & Bug Hunting Tool
76
Defendly
94
SecuriScanX
46
CyberPost Lab
73
Malware & Vulnerability Scanner
141
IntegSec CSP Tester
122
Website Security Scanner
71
CyberGuard: HTTP Security Header & Vulnerability Scanner
180
FortiDAST Web Application Scanning
112
OWASP Penetration Testing Kit
20,000+
NavSec Vulnerability Scanner
167
JS Vulnerability Detector
1,000+